7 min read
Spear Phishing vs. Phishing: The Difference And How To Prevent It
![]() Julia Chester
on Apr 17, 2020
Julia Chester
on Apr 17, 2020

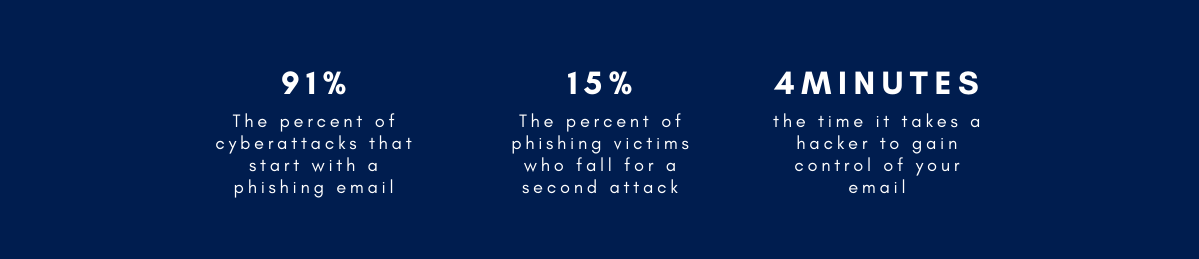
As many companies shift their operations online (and their employees shift into their “daytime jammies”) so too must their attention shift to cybersecurity. In our current COVID-19 conundrum many companies are moving strictly online. With these moves, data protection is more important than ever. Small and Midsize Businesses (SMBs) are no exception. Despite the fact that 67 percent of SMBs experienced a cyberattack last year (according to Keeper Security’s report of 500 senior SMB decision makers) 66 percent still believe that a cyberattack is unlikely and 60 percent do not have a cyberattack prevention plan in place. No company is too big or too small to be hacked and the results can be devastating. The average cost of a cyberattack on SMBs is $200,000, after which most companies must close shop. Phishing is an issue we all face. So, let’s face it, shall we?
In this article we will discuss Phishing and Spear Phishing attacks, and step by step instructions on how to prevent you and your company from being victims of one. While everyone, from your average Josephine to your top CEOs and tech pros have been duped by these covert attacks, we will show you what you need to know to keep you and your company safe. No one wants to be the click that cripples the company. Read along to avoid being your attacker’s catch of the day.
What is Phishing?
Phishing is the act of trying to obtain sensitive information (think login credentials and credit card details) from you by an sending email in which the sender poses as a trusted source (Facebook, Netflix, Bank of America) with the goal of financial gain or destroying your hard-earned company's reputation.
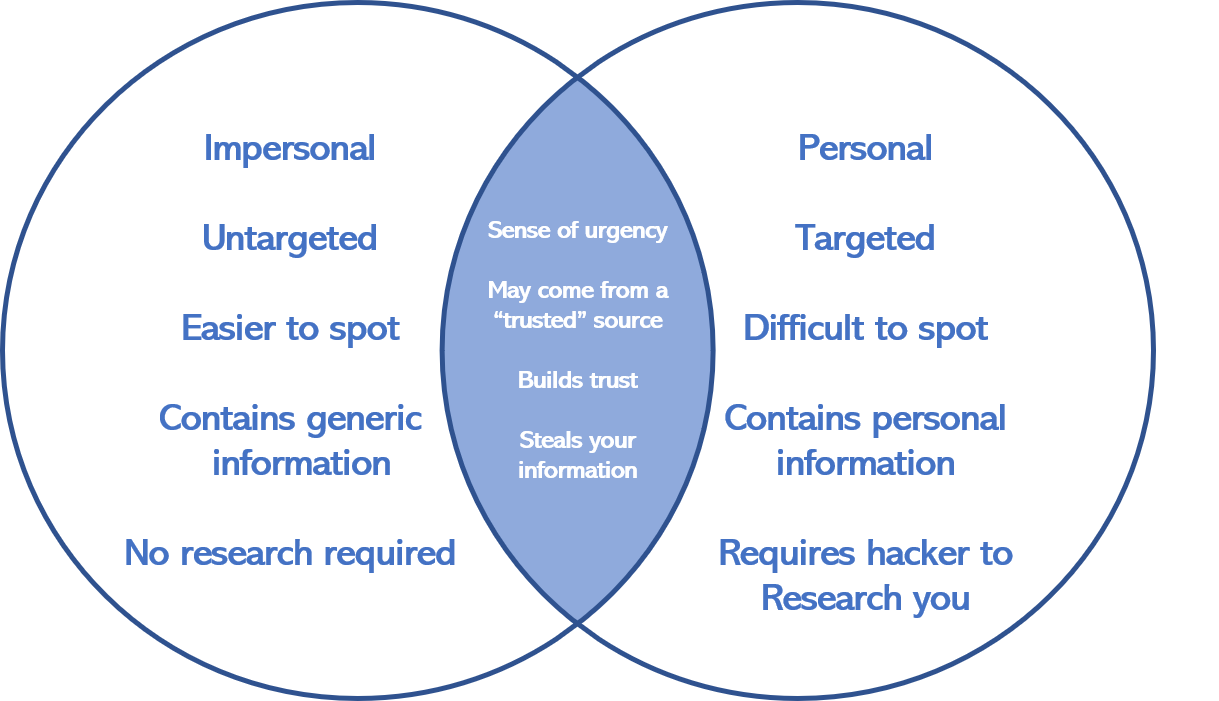
Phishing as a whole is large in scope and general in its aim: gathering sensitive information. Imagine a commercial fisherman casting a wide net. He then lies in wait as the fish come in (hint: you’re the fish). The larger the net, the larger the potential harvest.
You can also think of Phishing in terms of recreational pole fishing. The target is not direct. The fisherman does not care if she gets a Sunfish or a Bass or a Trout. She simply wants a fish and her hook is only made sweeter by using bait.
Phishing Example
Out of the water and on dry land, Cyber Phishermen use a similar approach by sending out mass emails to cast wide nets and bait their prey. The more Phishing emails attackers send out, the more clicks they will get, resulting in more sensitive information being compromised. These Phishing emails are often baited to lure you in, posing as trusted brands (think Facebook, PayPal, etc.) you feel comfortable with.
You’ve probably seen these (often horrible looking) emails from someone posing as Netflix or Bank of America asking you to reset your password, or claiming that your credit card was declined, right? Look how BAD this one is, posing to be from PayPal but there are several Brandon's as the recipient!
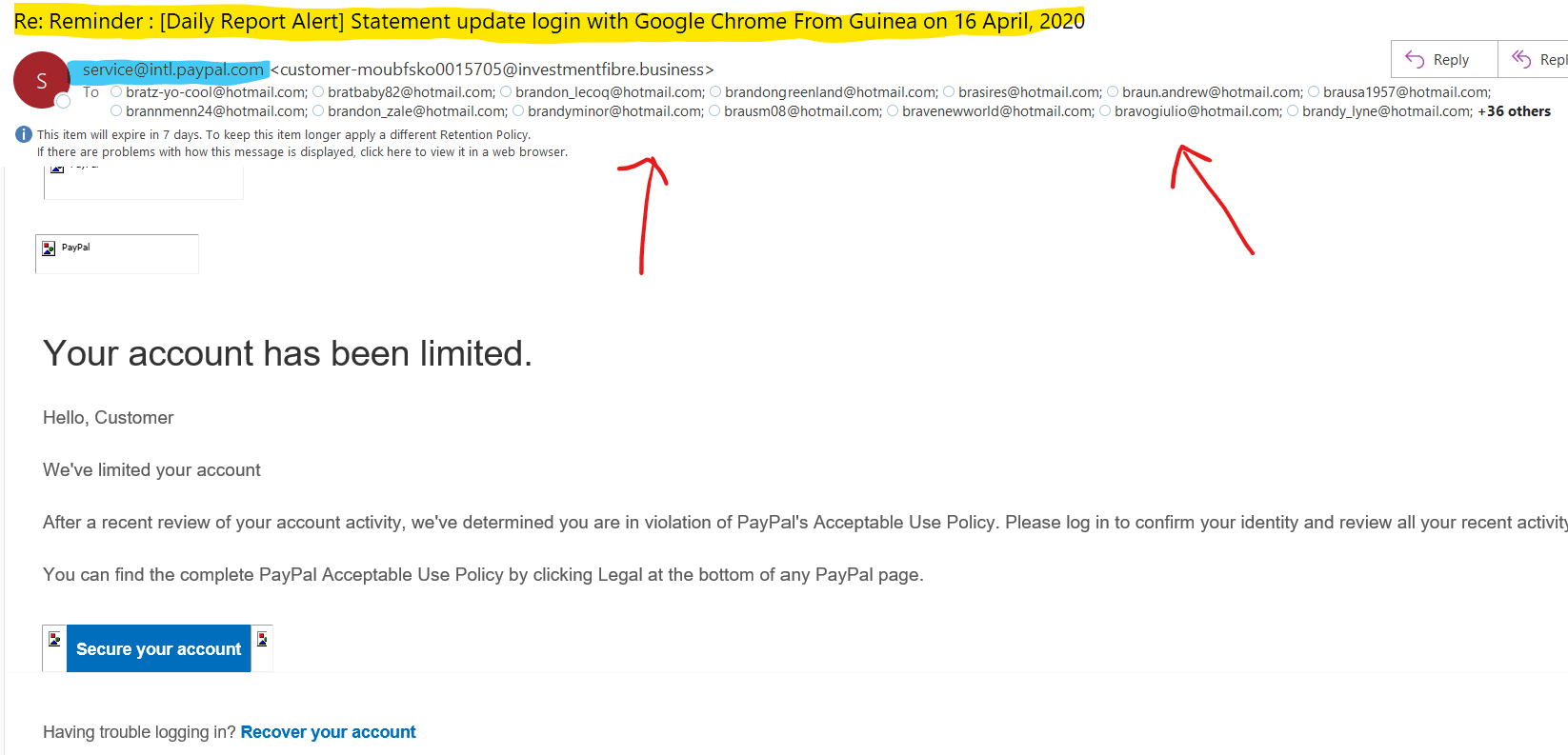
We all get umpteen similar emails daily. Simple requests made to look safe and innocuous. Yet with Phishing, they are anything but. Most of the time these emails are obviously fake. They contain unmatched company fonts or poor spelling and grammar. However, since you almost always notice the glaringly bad phishing emails, you might not notice the really good ones, the ones that get you, like the one below:
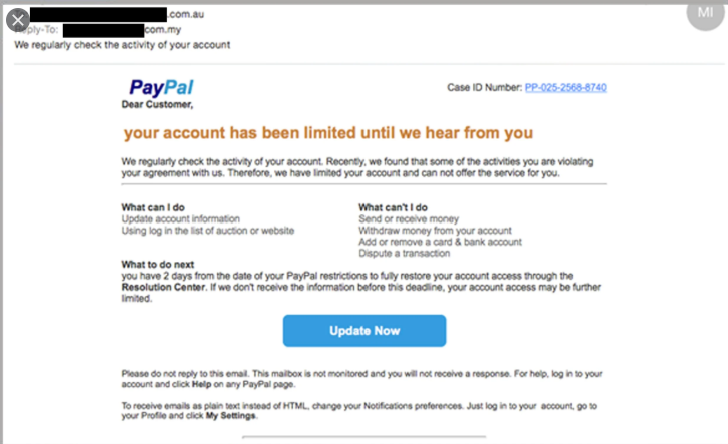
The good news? Phishing has become more mainstream. There aren’t many people these days who haven’t taken a comedic dive into their Junk Email to find requests for aid from foreign princes or emails from Bank of America telling you your account needs attention. In our increasingly tech driven world, we are all getting a little tech savvier (and so is our email. Hello Junk folder!). Huzzah!
The bad news? As Phishing has become more mainstream and society has become better at spotting attacks, attackers have had to innovate. How? Spear Phishing.
What is Spear Fishing?
Spear Phishing is a highly targeted attack on an individual or organization. The intent is far more calculated and malicious in nature than Phishing. Attackers aim to glean extremely sensitive personal or company information (like trade secrets, stock information and more) or install malware on you or your company’s network. How do they do it? Unlike normal Phishing where an email is sent to untargeted masses, Spear Phishers know exactly who they are targeting: you.
Spear Phishing is singular in scope. To continue our fishing analogy, imagine (you guessed it!) a spear fisherman. A spear fisherman is not out lollygagging about waiting for a rustle in a net. They are zeroed in on their prey, stalking them. They know everything: their habits, their locales, their weaknesses. So do your attackers.
Spear Phisherman use existing information you have innocently placed on the internet against you (think social media shares and online profiles). Like a spear fisherman throwing their spear, the aim is exact. So too is the Spear Phisher’s attack on you. You are the target and to their trained hand, you may be an easy one. Even top executives and tech savvy personnel alike who have been trained to avoid cyberattacks have fallen prey to Spear Phishing (think Google, Facebook and Apple, to name a few).
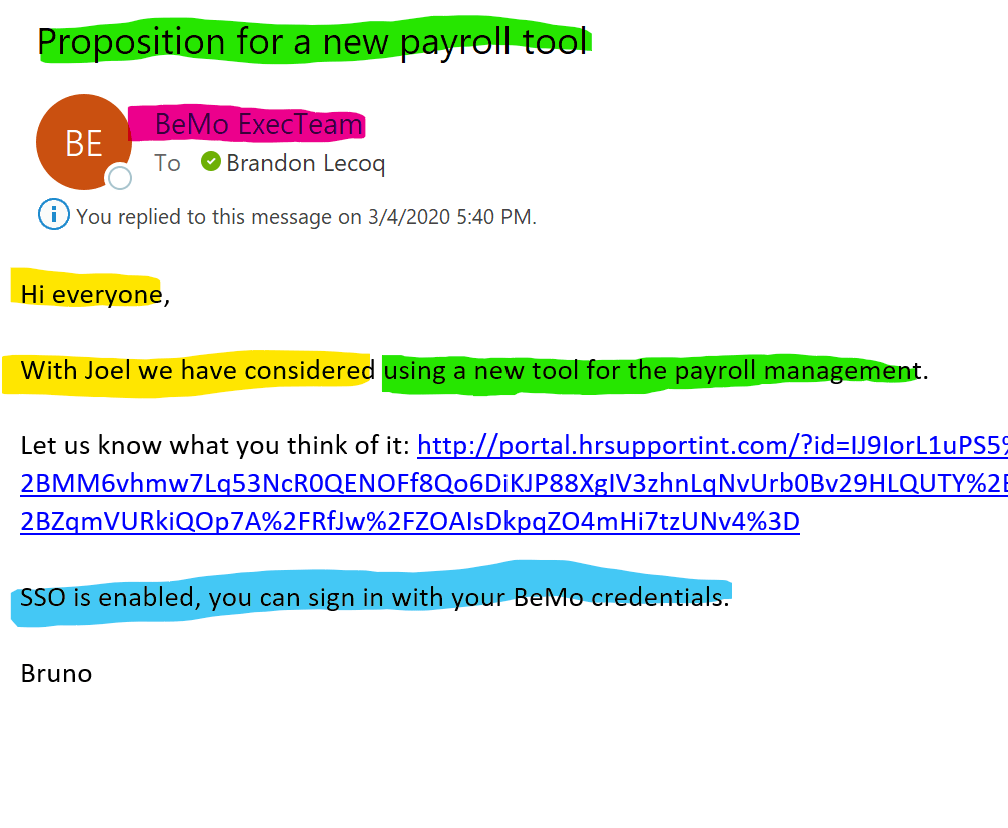
Spear Phishing Example
Here is an example using Microsoft’s Office 365 Phishing Attack simulator.
- Bruno and Joel are the co-owners of BEMO, which can be easily discovered by reading the titles of our employees on LinkedIn. A company-wide email stating the Bruno and Joel have considered something new is a very normal email to receive and would not raise any red flags for the reader.
- BEMO is a cybersecurity company, and the email contains industry jargon. ‘SSO’ stands for Single Sign-On, which means you have the same username and password for all your accounts.
- The topic of the email is innocuous. It is not asking us to reset our passwords. There’s no declined credit card. It’s simply a request to check out this new payroll tool. People send each other links to check out websites every day. It’s completely normal!
- The sender is ‘execteam@bemopro.com’ which is a real address within our company and didn’t come from a normal phishing email like ‘4tjgnd@netttflix.com’
There are only two things that would need to change to make this 100% believable:
- The link shared is very long which looks weird, therefore drawing some level of suspicion. Still, you’d probably click on it anyway. I mean, it’s just one weird link, right? Plus, it’s coming from your CEOs, whom you trust. Instead of inserting a long link, a true spear-phishing email would include a ‘hyperlink’ instead, so that the reader wouldn’t see the full URL.
- The email was only sent to one employee. This can EASILY be glimpsed over, but the tone of the email reads as if Bruno is writing the message for multiple people to check out, so you’d think some other people in the company would be recipients as well, right? To provide more validity, an attacker could easily pick a few other people in our company via a quick LinkedIn perusal and add them to the email.
How hard was that? All I would need to do to create such an email is:
- Creep around on LinkedIn
- Find your email (thousands of tools to this, your sales team already knows how)
- Write a ‘check out this tool’ type of email
- Take advantage of a lack of Multi-Factor Authentication (more on that below)
- Infiltrate an email server without DKIM, DMARC, or SPF enabled (more on that below. FYI, most companies don’t have this enabled.).
O.K. Now that we are sufficiently scared to swim in the cyber waters, let’s take a moment to dig a little deeper into our Phishy friends:
OK, So What Do I Do?
If you are feeling hopeless, fear not. While Phishing attempts likely won’t cease in the near future, there are certain things you can do to protect yourself:
- Get completely off all social media.
- Remove all information that has ever existed about you from the internet.
- Smash your computer.
- Hide under the covers.
Simple, right? Nope.
Beyond being difficult, these tactics are completely unnecessary (though who hasn’t dreamed of going full Office Space on their desktop?). What would we do without our mid-day dog videos on YouTube or the connection of social media? There is no need to deny the world your Insta-worthy shares or to deny yourself access to any site that requires a login (Hello, wine of the month club!). You can, however, do a few small things that make a big impact on whether you become the catch of the day or the one who got away.
How to Prevent Phishing Attacks
Unless you’re planning on skipping town, you’re probably pretty attached to your name and identity (unless, of course, your name is Mr. Dumass ). Plus, no one wants to be the big fish whose getting caught takes the whole company down, right?
To prevent phishing and spear phishing attacks, enable do 5 following things:
- Enable 'Anti-spoofing' tools on your Email & DNS - DKIM, DMARC, and SPF
- Enable Microsoft's Anti-Phishing tool called Office 365 Advanced Threat Protection
- Turn on Multi-Factor Authentication for all users
- Enable Microsoft's email encryption tool called Office 365 Message Encryption
- Block all traffic from IMAP, SMTP, and POP protocols
1. Enable DKIM, DMARC, and SPF:
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC), are Domain Name Server (DNS) and email protocols that ensure that the sender of the email actually is who they say they are and not pretending to be someone else (which is called being ‘spoofed’).
Read our How to Enable SPF, DMARC, and DKIM blog post for instructions on how to set this up using a free tool we use daily called MxToolbox.
2. Enable Office 365 Advanced Threat Protection
Office 365 ATP protects your organization against phishing attacks and malicious attachments. Watch the video below to see how it works:
A very recent example of ATP's prowess occurred earlier this month when, Microsoft reported "an attacker launched a spear-phishing campaign that lasted less than 30 minutes. Only 135 customer tenants were targeted, with a spray of 2,047 malicious messages, but no customers were impacted by the attack.
3. Enable Multi-Factor Authentication (MFA)
81% of data breaches are due to weak, reused or stolen passwords, which is how attackers deploy phishing and spear-phishing attacks.Microsoft has made it insanely easy with their Microsoft Authenticator app, approving an MFA request is as simple as hitting ‘Accept’ on your device (even without cell coverage). No more entering randomized codes and toggling between apps, ever.
Read our blog post, Office 365 MFA Setup: Step-by-Step Instructions to set this up.
4. Enable Office 365 Message Encryption
With Office 365 Message Encryption (OME) you can send encrypted emails to people inside and outside of your company without needing a 3rd party tool regardless of the destination email address (Gmail, Yahoo! Mail, Outlook.com, etc). Here is a video of how it works below:
5. Block all traffic from IMAP, SMTP, and POP protocols
Internet Message Access Protocol (IMAP), Simple Mail Transfer Protocol (SMTP), and Post Office Protocol (POP) are communication protocols created between 1981 and 1988, so its pretty old technology. These protocols don't support the multi-factor authentication (MFA) technology we have today and are now considered 'legacy authentication' measures.
This means that it doesn't matter if you have MFA because attacks that use these three channels will bypass MFA, so you have to close these ports! For further reading, check out our blog post, Azure MFA Loophole: Why am I still under attack?
Don’t be the catch of the day, be the one who got away!
Are you at risk of getting phished? Take this 5-minute quiz we created to see if you are at risk of getting hacked.
Oh dear, don't want to do this yourself? We can set all of this up for you with our email security plan or you can schedule a quick call with you to advise you on how to deploy this.
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Office 365 MFA Setup: Step-by-Step Instructions
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)



Leave us a comment!