5 min read
IT Security Policy: Why You Need One (+How to Create Yours)
![]() Julia Chester
on Oct 15, 2021
Julia Chester
on Oct 15, 2021

What's your company's security policy?
How do you classify your data?
How do you manage your data?
Most importantly: How do you protect your data?
If these questions leave you wanting to pull an ostrich and bury your head in the ground, come on up for air. This blog will show you the ins and outs of the importance of a company IT policy and help you to create your own. Let's dive in, shall we?
Company handbook introduction
So, your company's IT security policy is a little less than lackluster, eh? First off, give yourself a little break.
As an SMB, it's hard to balance the Nice to Haves with the Need to Haves. There's always too much on your plate and it can be hard to focus on what matters most. But as you grow, that balance changes and security policies are something that becomes concretely bucketed in the Need to Have side of things.
If you have ignored security up until now, you're not alone. In my interview with Carol Bubar, BEMO's Program Management and Operational Excellence Leader (aka she keeps everyone at BEMO in lock-step for every project we have. She's amazing) assured me that "For the most part, people are kind of starting from scratch. A lot of people have good ideas around passwords. They might have defined how they want passwords or how they want to manage their passwords. In some cases they don't. They might have email signatures and pieces of the different policies, but maybe not documented or not all in one place."
Does this sound like you? That's A-OK but now that you know you need a security policy and a resulting handbook (so that company-wide, the policies are clear), how do you make one? Security may not be your forte but luckily, it is ours. We're happy to go over your current security policies and advise you in a free one-hour consultation (click on the image below) or click here and we can oversee the entire project.
What is a security policy?
OK, now that you know that you need one...what is an IT security policy exactly anyway? Carol says: "Basically think of it [your IT security policy handbook] as a combination of several different policies. So, it's really helpful, kind of proactively to think about your data and how you kind of classify your data, how you manage it and how you protect it. It's just a little bit of process and definition, business rules and policies around that management, and protection of your data. That's the intent of the handbook."
Here's the full 5-minute interview:
Get a download of the full transcript here.
OK, that doesn't sound so bad, right? Think of it as your spring or fall cleaning for your security. Most companies could use a fresh coat of paint (or maybe a first coat of paint) when it comes to security. Take some time to sit down and think about your business needs when it comes to security. Do you need proof of your security standing as a business? You'll want to visit our Security Attestation Letter blog for a free template. Do you need to have multiple types of employees (contract, full-time, part-time) with differing access needs? How is your data protected, if at all? Gather your leadership team and start to suss out what you need to be compliant with and what you need to be secure.
Need help? We are experts in creating company security policies and handbooks so that everyone is on the same page. Reach out for a free 1-hour security consultation with Brandon.
IT security policy handbook: How to make your own
Think of your IT Security Policy Handbook as your Emergency Planning. While the goal of security is to avoid issues, things inevitably come up. Laptops are stolen, power outages happen...life has a way of getting in the way of our plans, right? So, what do we do? Plan for broken plans! The Handbook is like your emergency evacuation route. It's better to have it in place before an emergency than after, right?
So you can create your own, Carol explains the Handbook a little further: "Basically you're trying to protect from having an incident. So, if you think about either physical or online incidents your laptop might get stolen. Maybe that's a physical incident. Well, it'd be great to know beforehand what you do if that happens. Right? You can't connect with your laptop. So, who do you talk to? How do you quickly process that? And likewise, on the electronic side, if there's a breach or if there's an incident, you know, thinking ahead of time and how many people know ahead of time, how to react to those sorts of things is also one of the added benefits of having it documented."
Can't argue that, right?
Here's a list of areas (straight from the IT Security Handbook we use for our customers) you'll want to cover when you create your IT Security Policy and Handbook:
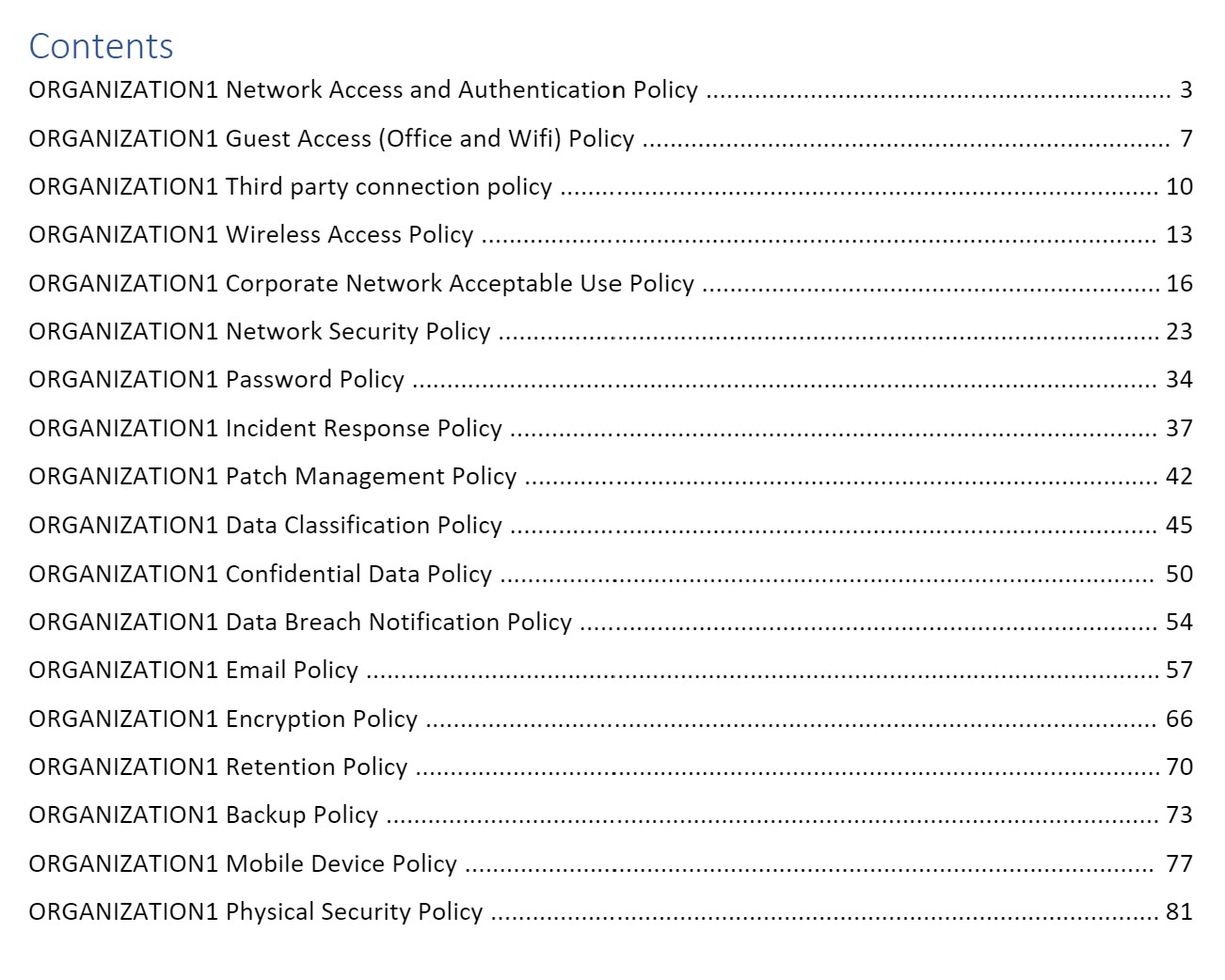
When you schedule your complimentary 1-hour consultation, we'll provide you with the entire template to work through with your company or with BEMO.
The best employee handbooks...
Just like anything with business, the best employee handbooks (especially IT handbooks) are specific to your business. You wouldn't use the same evacuation route as a company across the street so your IT Security plan will be completely unique as well. Your handbook will cover everything from company screensaver password protocol to disaster protocol and each and every aspect will be completely specific to your company so take your time and make it your own.
IT security service
Like we said, the best handbooks are completely individualized and no one knows your business like you do. Still, while you know your business backwards and forwards, security might feel a little more foreign. So, as IT is our forte, we offer IT security as a service so you can focus on your business instead of learning a whole new world of cybersecurity. Since we created the IT security policy template, we have worked with countless companies to go through each and every angle of their specific policies. There's no one-size-fits-all.
Does this sound like wayyyyyyy too much of an endeavor? We get it. It sounds pretty overwhelming BUT, when I asked Carol how long someone could expect to spend on creating company IT policies she said: "I'd say from the template and our starting point, we have maybe a 75% starting point, 80% starting point. So, it's really just putting the meat on the bones. It depends on basically the client's bandwidth to do a couple of reviews. Usually we'll pull initial data in, we'll get a good draft and then we'll fine tune it with a couple of reviews and then it'll be ready to go". Pretty easy, huh?
Cloud Security Handbook
Last thing's last: Does my handbook need to live in the cloud? While we have customers who still work with a hybrid setup, they've worked hard with us to get off of on-prem and to the cloud and the hybrid is the halfway point. Overall? Our vote is for the cloud. While it may seem obvious that a cloud-based company would vote for all cloud, all the time, we definitely think that having a hard copy on premise is a great idea...and...
The benefit of the cloud is that you can disperse knowledge quickly and also guard materials just as easily. Keeping your whole team in the know about what to do and when is totally possible when the document lives in cumulus land. If you're still on-prem, don't worry. Start where you are and go from there and, as always, we are here to support you along the way. Start a chat or get your free 1-hour cybersecurity review by clicking on Brandon's picture below. Best of luck!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)





Leave us a comment!