
We do our best to keep our articles updated. Please note that Microsoft Active Directory has been renamed to Microsoft Entra ID.
At BEMO we’re masters of migrating Domain Controllers to Azure. During our discovery calls with the customers, it's obvious there's a lot of confusion about all the different options around Active Directory (AD) which is now known as Microsoft Entra ID. Below we'll explain their differences to help you decide what you need.
- Active Directory (AD)
- Azure Active Directory (AAD)
- Hybrid Azure Active Directory (Hybrid AAD)
- Azure Active Directory Domain Services (AADDS).
Active Directory (AD)
NOW MICROSOFT ENTRA ID
Microsoft Active Directory (most often referred to as a domain controller) is the de facto directory system used today in most organizations. Active Directory is excellent for managing the authentication and authorization functions for users and computers within an organization.
Its reliance upon member computers permanently joined to a domain and protocols such as LDAP for directory querying and Kerberos for directory authentication are no longer suitable for the modern Internet-centric, mobile style of work environment becoming the norm today.
Think of Active Directory as on-premise only, which means all of your authentication infrastructure is running on hardware in house.
Azure Active Directory (AAD)
Azure Active Directory (AAD) is a version of directory services “in the cloud” hosted on Microsoft Azure. AAD does have quite different capabilities and features compared to Windows Server Active Directory (AD). Its primary function at the moment is to manage users and the myriad of devices (Windows, Apple and Linux PC’s, tablets and smartphones, etc.) that users are employing in their work and social lives, particularly for remote users.
AAD is blurring the distinction between “on-premise" and “remote” users. AAD is the authentication and authorization mechanism for not only Azure, Office 365 and Intune, but is capable of tying in many other third-party authentication systems.
Think of Azure Active Directory as cloud only, which means if you have legacy software you will need to go with Hybrid Azure AD (HAAD).
Hybrid Azure AD (Hybrid AAD)
Hybrid Azure AD is used when you have your local Active Directory (domain controller) on-premise and want to synchronize your data to Azure Active Directory. Instead of having two sets of credentials in two different places, you can add it in the ‘onsite’ domain controller, and it will replicate to Azure AD with the help of a Microsoft software add-on called Azure AD Connect.
Hybrid Azure AD is the first step in achieving one single identity. Today, most of our clients have one set of credentials to log on to their laptop and one set of credentials to log on to their email hosted on Office 365. With Hybrid Azure AD, you can set up the synchronization to Office 365 and manage the users on-premise, using your existing local Domain Controller.
You have two options:
Option #1: You keep your ‘on-premise’ domain controller within your physical location, and install AD Connect to synchronize your users, and their passwords, with Azure AD.
Option #2: Move your existing ‘on-premise’ domain controller into a virtual machine hosted on Azure, install AD Connect to synchronize with Azure AD, and create a VPN connection between your office and the Azure datacenter where your domain controller is now hosted.
Azure Active Directory Domain Services (AAD DS)
Azure Active Directory Domain Services (AAD DS) is a standalone service in Azure that enables a domain controller for virtual machines in Azure, without setting up a standalone server as a domain controller. It creates a domain controller as a service, so you don’t need to worry about downtime, patching or other things.
What it does is that it syncs users, groups, and passwords from Azure AD to makes it available for the virtual computers in an Azure network.
You can use the Active Directory Administrative Center or Active Directory PowerShell to administer managed domains. With AADDS,
- You will not need any virtual machine to host your Active Directory
- You can use the same groups and users as in your Azure tenant for your virtual machines.
- Passwords from your Azure tenant are replicated to your domain.
- Your Azure AD Domain Services managed domain is deployed in the same Azure region as the virtual network you choose to enable the service.
- AADDS is a continually billable service (you cannot turn it off).
AADDS is not Active Directory as you know it. AADDS:
- Does not support replication.
- Cannot set up as a trusted domain to other domains
- No Domain/Enterprise admin privilege
- Schema extensions are not supported
- AD domain/forest trusts not supported
- LDAP write not supported.
- Certificate/Smartcard based authentication is not supported by Azure AD Domain Services.
- Does not support managed service accounts
AAD DS is great for virtual machines hosted in Azure, simple to set up and works well with your Azure AD. AAD DS does NOT replace a proper domain controller and does not work with managing users and computers like with Windows Server Active Directory. AAD DS works great if you plan on a cloud-only strategy with limited users, and not GPOs.
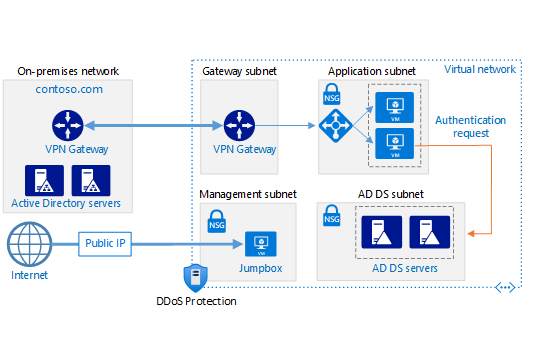 Diagram from Microsoft's article on how to deploy AD DS in Azure virtual network. Click here to visit it.
Diagram from Microsoft's article on how to deploy AD DS in Azure virtual network. Click here to visit it.
To date, we mostly implement Hybrid Azure Active Directory by moving our clients’ existing on-premise domain controller into a virtual machine hosted on Azure, using an availability set for fail-over and redundancy capability, install AD Connect to synchronize with Azure AD and create a VPN connection between their office and the Azure datacenter. With this option, you can leverage the power of Azure while making sure your legacy application will still run.
Questions? Schedule a free meeting with us by clicking the button below:
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Office 365 MFA Setup: Step-by-Step Instructions
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)




Leave us a comment!